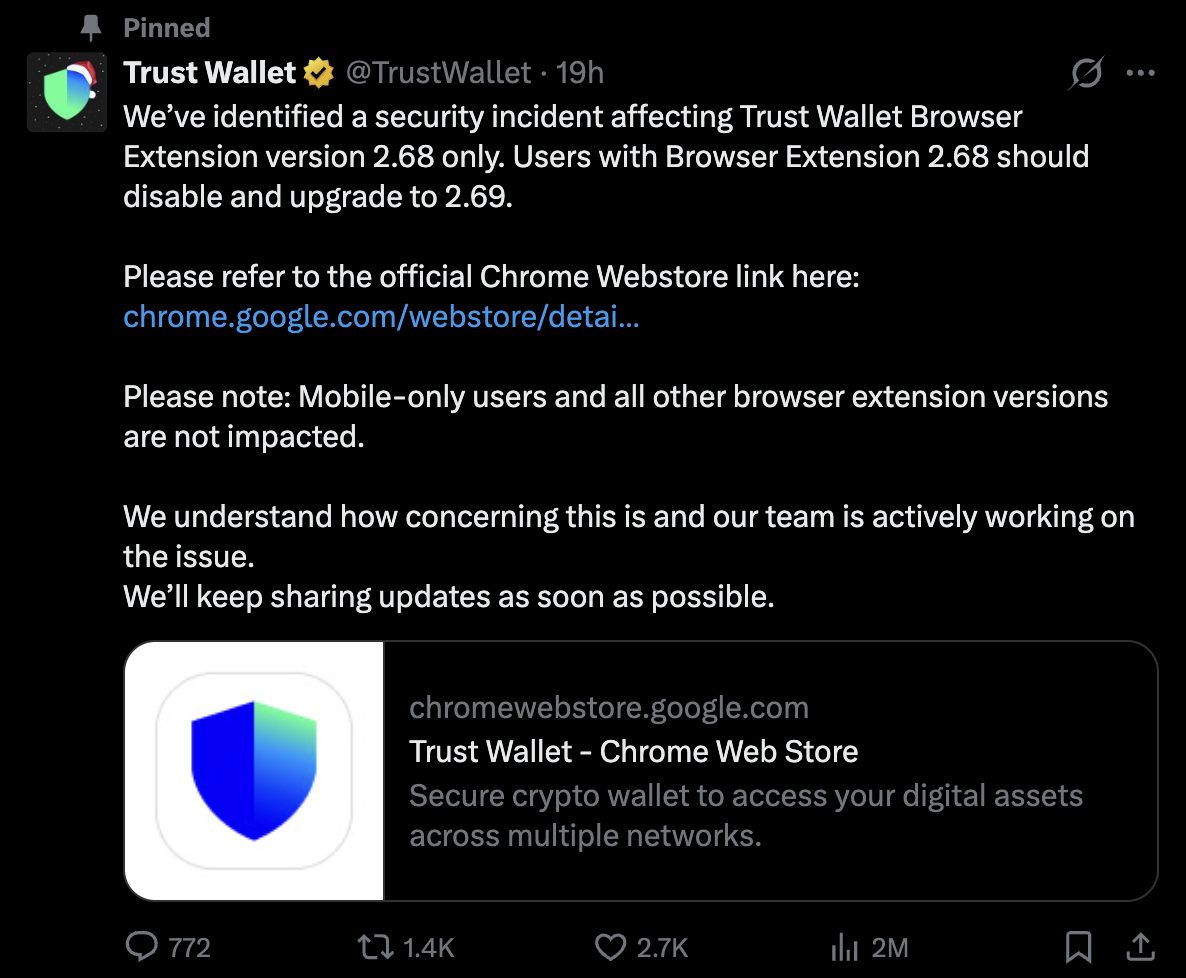
25 December 2025, Trust Wallet disclosed a security incident affecting version 2.68 of its Chrome browser extension. The compromise enabled unauthorized access to private wallet credentials and resulted in the theft of cryptocurrency from affected users.
While Trust Wallet did not publish an official loss figure, independent blockchain investigators estimated that approximately USD 7 million in digital assets were stolen based on on-chain analysis of drained wallets. The incident was first reported by industry media, including CoinDesk, following Trust Wallet’s public disclosure on 25 December 2025.
The breach did not involve a failure of any blockchain protocol. It originated from a compromised software update distributed through a trusted channel. From an AML perspective, the incident became materially relevant once stolen assets entered on-chain transaction flows and began interacting with the broader ecosystem.
Timeline of the Trust Wallet Extension Breach
Malicious activity associated with Trust Wallet browser extension version 2.68 began on 24 December 2025. Affected users reported unauthorized wallet drains shortly after interacting with the extension.
On 25 December 2025, Trust Wallet publicly acknowledged the incident in an official statement published on its verified X account. The company confirmed that:
- Only browser extension version 2.68 was affected
- Users were advised to disable the extension and upgrade to version 2.69
- Mobile users and other extension versions were not impacted
This public disclosure marked a clear shift in compliance expectations. Once an incident is acknowledged, regulated entities are expected to identify and manage potential exposure to related illicit fund flows.
How the Trust Wallet Extension Was Compromised
The incident resulted from a malicious browser extension update that contained unauthorized code capable of extracting mnemonic seed phrases when users unlocked or imported wallets.
From a financial crime classification standpoint, this constitutes a credential compromise leading to theft of assets. Once private keys were exposed, attackers exercised full control over the affected wallets and transferred funds without user authorization.
At the moment of unauthorized transfer, the assets became proceeds of crime. Any subsequent transaction involving these assets created potential AML exposure for downstream entities.
Estimated Loss and Attribution
Trust Wallet did not release an official estimate of total losses. Independent on-chain investigators tracked unauthorized wallet drain activity associated with the compromised extension and aggregated the value of stolen assets at approximately USD 7 million.
This estimate is based on:
- On-chain tracing of unauthorized transfers from affected wallets
- Aggregation of balances across multiple blockchain networks
- Analysis conducted by independent investigators and cited by industry publications
From an AML perspective, the precise figure is secondary. What matters is the confirmation that a material volume of illicit funds entered transaction flows and required monitoring, investigation, and risk assessment.
On-Chain Fund Flow Patterns After the Theft
Analysis of on-chain activity following the incident reveals patterns consistent with wallet takeover events.
Stolen assets were transferred rapidly after credential extraction, often within minutes. Funds were fragmented across multiple addresses and, in several cases, routed through swaps or cross-chain mechanisms. These behaviors are commonly observed in laundering typologies designed to reduce traceability and delay detection.
Identifying such activity requires behavioral and linkage analysis rather than static address screening.
How Stolen Assets Created AML Exposure
AML exposure did not arise at the moment of the hack itself. It emerged once stolen assets began interacting with other wallets, protocols, and services.
Exposure occurred when illicit funds:
- Passed through intermediary wallets
- Interacted with decentralized protocols
- Reached centralized exchanges or custodial platforms
Entities processing these transactions faced compliance obligations regardless of whether they had any connection to the original security incident. Public confirmation of the breach further increased the expectation that exposure would be identified and managed appropriately.
Compliance Obligations for Exposed Entities
Once exposure to stolen assets is identified or reasonably suspected, AML obligations are triggered.
Depending on jurisdiction and entity type, these obligations may include:
- Enhanced transaction review
- Risk scoring and internal escalation
- Documentation of investigative steps
- Suspicious activity reporting where required
In cases involving publicly acknowledged incidents, regulators expect compliance teams to demonstrate that reasonable monitoring and detection controls were in place and operating effectively.
Role of Blockchain Analytics in Incident Response
Managing AML exposure following a wallet compromise requires continuous transaction visibility and analytical depth.
Scorechain’s blockchain analytics platform enables compliance teams to:
- Trace illicit assets across multiple transaction hops
- Identify address clusters linked to compromise events
- Analyze transaction velocity, fragmentation, and laundering behavior
- Monitor exposure across multiple blockchain networks in a unified environment
This approach allows teams to identify both direct and indirect exposure and to assess risk based on transaction behavior rather than isolated wallet addresses.
Limitations of Static Screening
Static address lists are insufficient in post-theft scenarios.
Attackers frequently rotate addresses and move funds through newly created wallets. Exposure often occurs several hops away from the original compromised address. Without transaction graph analysis and continuous monitoring, these risks may remain undetected until funds have already progressed through the ecosystem.
Effective AML controls must therefore adapt dynamically as illicit funds move on-chain.
Key AML Takeaways From the Trust Wallet Incident
The Trust Wallet browser extension breach highlights several realities for compliance teams:
- Illicit funds can originate from non-custodial wallet environments
- AML exposure emerges downstream during asset movement
- Detection depends on behavioral and linkage analysis
- Cross-chain visibility is essential for accurate exposure assessment
- Blockchain analytics is a foundational control for post-incident response
Conclusion
The Trust Wallet browser extension breach in December 2025 demonstrates how application-level security failures can translate into material AML risk across the crypto ecosystem.
Once stolen assets entered on-chain transaction flows, responsibility shifted to compliance teams to detect exposure, assess risk, and take appropriate action. Blockchain analytics platforms such as Scorechain provide the analytical foundation required to identify illicit fund movement and support informed, risk-based compliance decisions following wallet compromise incidents.
.png)




.png)














