On December 30, 2025, Unleash Protocol reported an incident involving unauthorized activity within its smart contract environment, resulting in losses estimated at approximately $3.9 million.
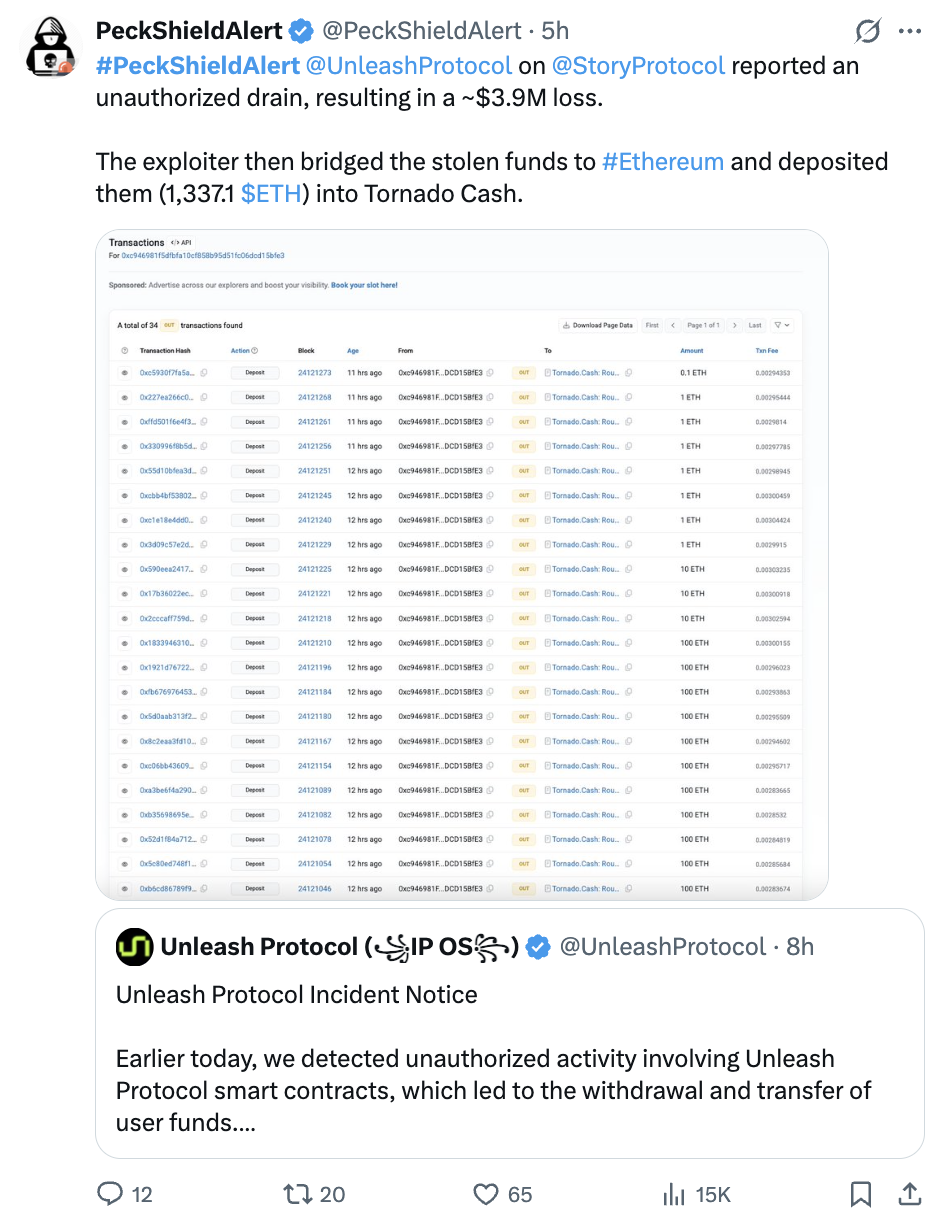
The incident was first flagged publicly by PeckShieldAlert, which reported that stolen assets were bridged to Ethereum and subsequently deposited into privacy infrastructure. Shortly after, Unleash Protocol published an official incident notice confirming the nature and scope of the compromise.
What makes this case notable is not only the fund movement that followed, but the origin of the incident itself. This was not a smart contract logic bug. It was a governance and permission failure that rapidly translated into downstream risk.
What Happened
According to Unleash Protocol’s incident notice, the team detected unauthorized activity involving Unleash smart contracts that led to the withdrawal and transfer of user funds.
Their initial investigation indicates that an externally owned address gained administrative control via Unleash’s multisig governance, allowing the attacker to carry out an unauthorized contract upgrade. This upgrade enabled asset withdrawals that were not approved by the Unleash team and occurred outside intended governance and operational procedures.
The assets identified as affected at this stage include:
- WIP
- USDC
- WETH
- stIP
- vIP
Following the withdrawals, the assets were bridged using third-party infrastructure and transferred to external addresses.
Unleash Protocol has stated that:
- The incident originated within Unleash’s governance and permission framework
- There is no evidence of compromise to Story Protocol contracts, validators, or underlying infrastructure
- The impact appears limited to Unleash-specific contracts and administrative controls
- The investigation remains ongoing
Governance Abuse as a Risk Multiplier
From an AML and investigations perspective, governance-driven incidents present a distinct challenge.
In this case, the attacker did not exploit a flaw in contract logic. They abused legitimate authority. Contract upgrades and withdrawals were executed as technically valid actions, despite being operationally unauthorized.
This is why governance abuse often escapes early detection. Transaction-level monitoring is designed to flag anomalous behavior, not misuse of administrative control. Yet from a risk standpoint, the exposure created can be immediate and severe.
A transaction can be valid on-chain while still representing unacceptable financial crime risk.
What the On-Chain Transaction Graph Shows
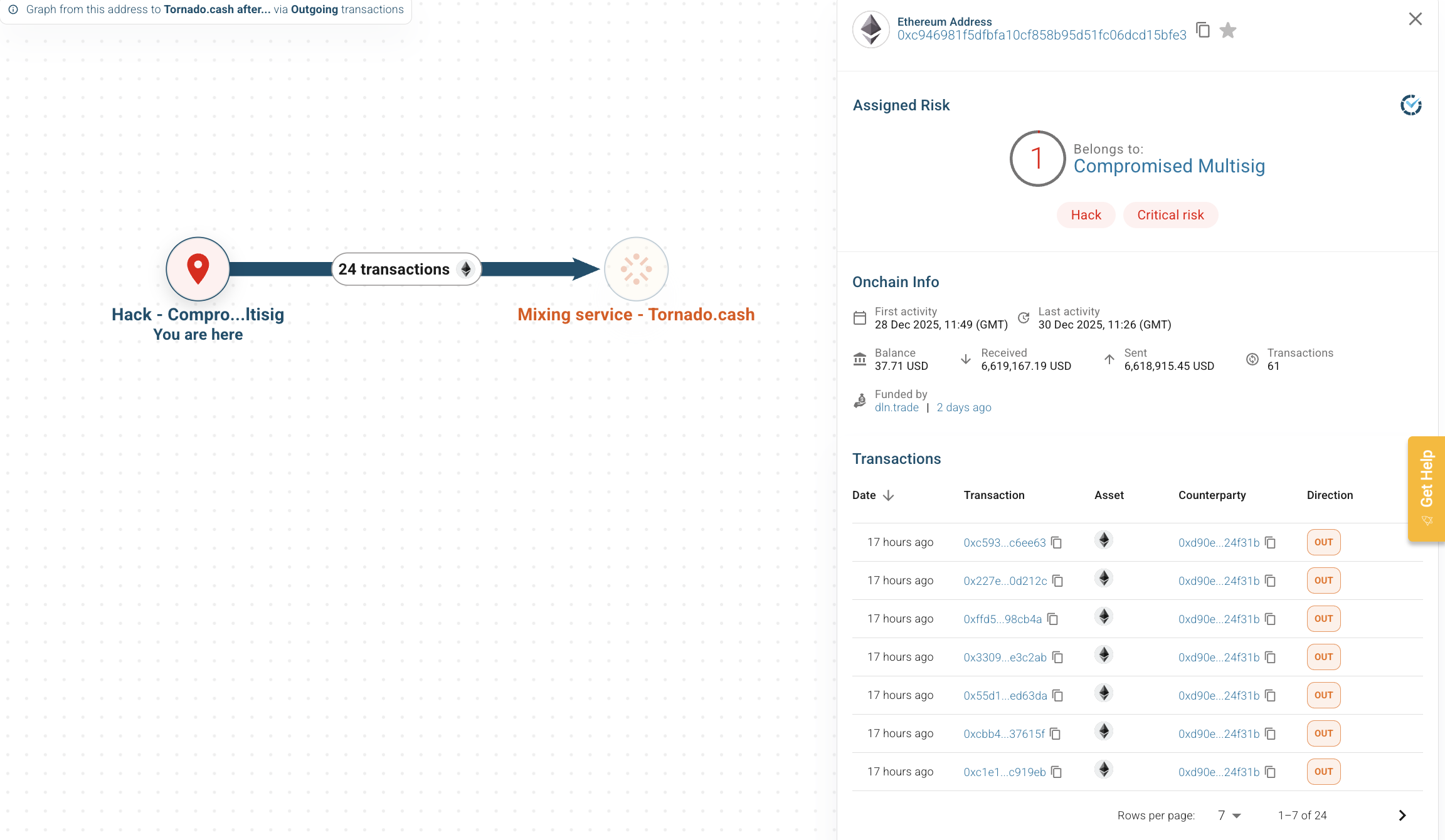
To validate post-incident fund movement, Scorechain analyzed outgoing activity from the compromised multisig address using a direct transaction graph.
The graph shows a clear and deliberate transaction path:
- The source address is identified as a compromised multisig, classified as critical risk
- 24 outgoing transactions were initiated from this address to the same destination cluster
- The transfers followed a consistent execution pattern within a narrow time window
- Funds were sent directly to a mixing service, without intermediate dispersion
This matters for two reasons.
First, the funds did not fragment across multiple counterparties. The activity followed a structured and intentional path, indicating immediate post-compromise decision-making rather than opportunistic movement.
Second, because the transactions originated from a compromised governance address, the activity appeared operationally authorized at the protocol level. This significantly reduces the effectiveness of conventional anomaly-based monitoring during the earliest phase of the incident.
Direct transaction graphing is a core investigative step for confirming post-incident fund movement before deeper exposure or network analysis is applied.
Why Early Exposure Matters
Once assets interact with advanced obfuscation mechanisms, response options narrow quickly.
Traditional monitoring approaches often escalate risk only after multiple hops or behavioral thresholds are crossed. In governance-driven incidents, this delay is amplified because the initiating actions appear operationally legitimate.
Without visibility into governance context and fund propagation, risk teams are left reacting after exposure has already materialized.
Early exposure analysis enables faster escalation, clearer investigative context, and more defensible decision-making.
Operational Takeaways
For exchanges, custodians, payment providers, and other ecosystem participants, this incident highlights several realities:
- Governance structures are a primary attack surface
- Risk can materialize before transactions appear suspicious
- Technical authorization does not eliminate downstream exposure
- Network-level context is essential for timely investigations
Incidents like this do not fail due to lack of alerts. They fail because exposure is identified too late.
Scorechain Perspective
The Unleash Protocol incident is not an outlier. It reflects how modern crypto risk increasingly emerges.
As governance frameworks grow more complex, they become attractive targets. When governance fails, the blockchain executes exactly as instructed.
Effective investigations require understanding who controls the system, how value propagates, and where exposure concentrates, not just which transactions occurred.
By the time assets are deeply embedded in obfuscation layers, the opportunity for meaningful intervention has already passed.
.png)
.png)


















